In the previous part of the report, we described the types of vulnerabilities, and presented selected numbers and data on the number of vulnerabilities by vendor, threat ranking and the most common attack vectors. In part two, we will focus on the topic of software updates, describe Zero-Day vulnerabilities, as well as discuss the metrics and mechanisms used to analyze the data.
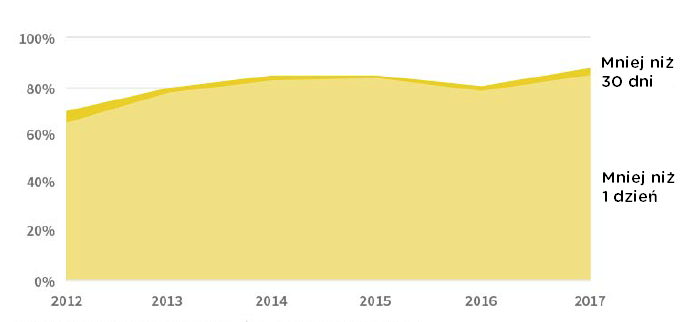
In 2017, 86% of all detected vulnerabilities received an update the very day they were disclosed. This statistic is 4% higher than in 2016, where the number was 81%.
The 2017 results clearly show that it is still possible to fix most security vulnerabilities by responding to them quickly.
The study noted that in 2017, more than 14% of all security vulnerabilities remained without a critical update for more than a day after the threat was detected. This percentage reveals a lack of adequate remediation resources on the part of manufacturers, a lack of proper procedures, uncoordinated processes for releasing updates, or manufacturers' failure to diagnose Zero-Day vulnerabilities in their software. In such cases, IT departments must have adequate security procedures and policies in place and, until patches are released, rely on their own skills.
Lack of priorities.
It is worth noting that some manufacturers have a policy of issuing only larger packages
with updates, rather than focusing on individual patches. The reason for this may be that developing smaller patches can be more complicated. On the other hand, larger updates are better managed.
The study reveals another interesting aspect. After 30 days from the date the vulnerability was discovered, more than 87% of the tested solutions had updates. Based on conversations with manufacturers, it was determined that for some of them it is not a priority to release a patch on the same day. Nowadays, this state of affairs is an undesirable phenomenon. Failure to respond quickly enough can mean big image, financial and economic losses for many companies around the world.
Since 2012, there has been a marked increase in the percentage of availability of updates for vulnerabilities detected on the same day. While in 2012 the value was slightly more than 60%, already in 2017 we meet a significant increase of more than 20%. This is a very good sign showing that there is a growing awareness among manufacturers to ensure "here and now" security.
The number of detected "Zero-Day" vulnerabilities in 2017 dropped from 23 to 14 compared to 2016. Interestingly, this statistic includes devices and operating systems, where the latter account for only 10-25% of the total vulnerabilities. Conclusion: the target of today's attacks is no longer operating systems alone, but the entire infrastructure including physical devices.
Metrics and mechanisms used in data analysis.
Secunia Advisory
The survey was based on the approximate number of safety events during the period. Safety events represent the number of administrative actions required to ensure the safety of a specific product during a specific period.
Secunia Vulnerability Count
The number of vulnerabilities is added to the Secunia Advisory database (https://secuniaresearch.flexerasoftware.com/community/advisories/search/) to indicate the number of vulnerabilities covered by Secunia Advisory. Using this number for statistical purposes is much more accurate than counting Common Vulnerabilities and Exposures (CVE) threat identifiers. Using vulnerability counts is not ideal, however, because they are assigned to a specific recommendation. This means that one recommendation can cover multiple products, or multiple recommendations can also cover the same vulnerabilities on the same code base that are common to different applications or even different vendors.
Common Vulnerabilities and Exposures (CVE).
Common Vulnerabilities and Exposures (CVE) is a publicly available directory of information
of known vulnerabilities and security gaps. CVE has, so to speak, become an industry standard for uniquely identifying vulnerabilities, which has received wide recognition in the security industry. Using CVE codes as vulnerability identifiers makes it possible to correlate information
about gaps between different security products and services. CVE information is attributed
In Secunia's recommendations.
However, the task of CVE identifiers is not solely to show the number of vulnerabilities. CVE is a very powerful tool for identifying one or more vulnerabilities and correlating them between different sources. The problem with using CVE identifiers to count vulnerabilities is that CVE abstraction rules can combine vulnerabilities of the same type in the same product versions into a single CVE. As a result, CVEs can often include too many vulnerabilities, which can result in a lower-than-expected demonstrated number of vulnerabilities during baseline.
Source: Flexera 2018 Survey and Report (www.flexera.com)