
Not too long ago, little attention was paid to systems management tools existing in the environment (planning and launching attacks on such environments). Unfortunately, this situation is becoming a thing of the past, and there should be a growing interest in the functioning of Systems Management software.
An example of this is the emergence of the SharpSCCM tool. This is not a tool for hacking into systems, as the discussions make clear[1],[2].
The tool is a collection of various functionalities that can contribute to gaining greater mastery over already acquired machines, using mechanisms that operate legitimately in an attacked environment, reducing the likelihood of detecting hostile activities.
An interesting aspect of SharpSCCM is the retrieval of CM Site organization information from the client machine, via local WMI queries. Already knowing SMSSITECODE and the name of the Management Point server selected for the client machine, an attempt is made to connect to the CM Site. When different roles are concentrated on a single server, this approach can be effective.
However, in the case of a multi-server organization, this is no longer the case:

The addressee of the call here should be the SMS WMI Provider, not simply Management Point. The functionality of the tool will be clearly limited in this case.
Analyzing the SharpSCCM source code, one can see an attempt to access the WMI space root\SMSSite_{SMSSITECODE}, which is mistakenly associated here with the Management Point function:

It can be expected that future versions of the tool will correctly identify the target server for WMI connections.
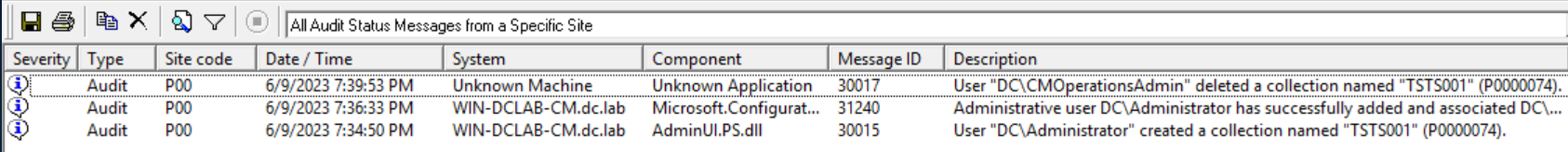
If you leave the Management Point on the server performing the SMS WMI Provider role (usually the Primary Site Server), the tool can create and destroy collections, for example, if there are sufficient permissions. Such actions are already recorded in the CM status message subsystem as an Audit type. In this case (event 30015), a TSTS001 collection was created using the Powershell command, and later destroyed (event 30017) by SharpSCCM (but we won't find out - we have an unknown application here).
Although the new tool does not break into Configuration Manager and is based on the known features of WMI, the risks should not be underestimated. It is prudent to isolate Primary Site Server and SQL Server from client machines (client machines do not need direct access to these servers).
__________________________________________________________________________
[1] https://www.securesystems.de/blog/active-directory-spotlight-attacking-the-microsoft-configuration-manager/
[2] https://github.com/Mayyhem/SharpSCCM/wiki
- Support and development of Microsoft and Nintex based applications
- Application design and development including digital processes
- Invoice management
- Requisition management
- Contract management
- Modern Intranet
ISCG sp. z o.o.
Al. Jerozolimskie 178, 02-486 Warsaw
NIP: 5262798378
KRS: 0000220621
Phone
Office +48 22 571 67 80
Sales +48 22 152 54 95
