
Fallback Status Point (FSP) server role is well known among Configuration Manager Admins. This server role helps with CM client installation errors, but uses unencrypted and unauthenticated communication. If FSP address (DNS name) is included in a command line then a client sends a message to FSP host.
It is interesting to check what is passed from invalid (not fully installed) Configuration Manager client to a CM Site and whether it reveals interesting information from security point of view.
LAB Setup – The following servers are installed and configured:
Server Name | CM Site role |
WIN-SCCMCB | CM Primary Site Server, SQL Database Server |
WIN-CMCBMR | CM Management Point, CM Distribution Point |
WIN-CMFSP | CM Fallback Status Point |
WIN-DC | AD Domain Controller |
For experimental purposes, CM FSP role was installed using dedicated server. This setup make easier to identify interesting network communication. A testing client machine is a standalone system (not a part of Windows Domain) to prevent it from reading configuration from AD.
Client installation files (ccmsetup.exe i client.msi only) were copied to a local folder, with no chance to obtain rest of necessary files for testing client system. The command line provided included incorrect Management Point name and true name of FSP to force client installation error.
Client installation failed, as you can see inside ccmsetup.log:

The testing machine sent a simple message, using http unencrypted and unauthenticated communication:

The most interesting part of network communication between failed client and FSP server can be captured. You can see some client data:

Captured data can be compared with file names inside FSP OUTBOX folder:
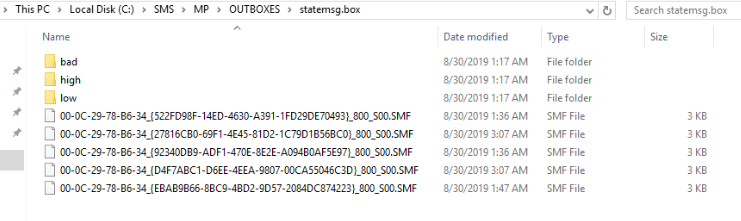
You can see MAC address and GUID of the „sender” are included in a file name.
Opening the file with name consistent with captured data, you can see:
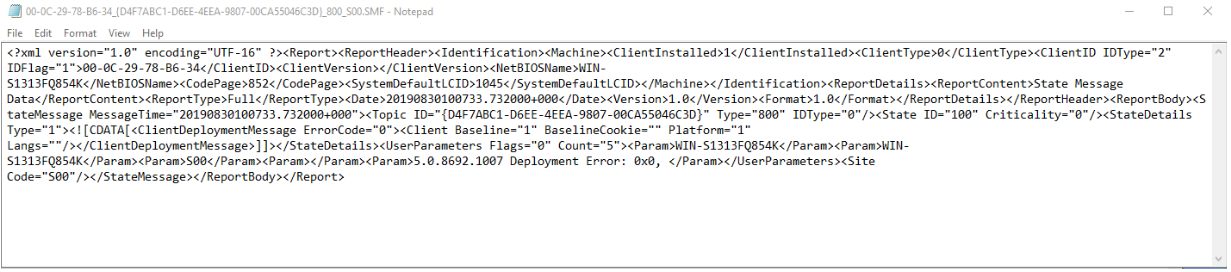
You can see MAC address and GUID of the „sender” are included in a file name.
Opening the file with name consistent with captured data, you can see:
 PL
PL