
MS Defender Antimalware can be managed with Configuration Manager. Endpoint Protection Point server role must be placed on selected Site System Server, client policies must be prepared and deployed. It was done, but some SQL tables with names starting with EP_ remained empty. EP_ThreatMetadata table may be used as an example:
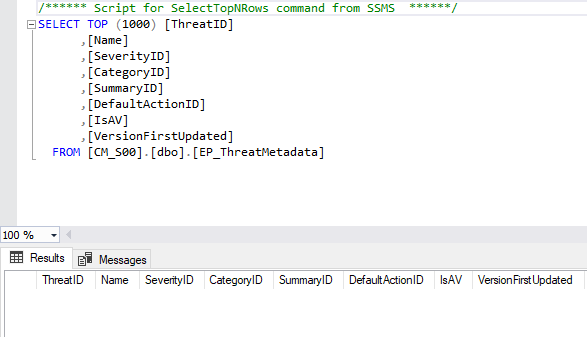
Empty tables are not expected. EP_ThreatMetadata table usually contains more than 200 thousand records.
In spite of empty tables, client workstations are correctly protected with Defender Av. Malware can be detected, but built-in Endpoint Protection reports remain empty. Configuration Manager is completely unaware of threat categories and severities (Tables: EP_ThreatSeverities and EP_ThreatCategories have no records). Endpoint Protection reports try to find data, but there is nothing to obtain.
Obviously, Endpoint Protection Point role is suspected. If you examine the role installation process, you can find System Center Endpoint Protection client is installed.

This (dedicated) server is not a Configuration Manager client and it is not included in CM Collection for Defender management. It cannot access Defender updates using default methods. The server have no access to Internet and WSUS server does not propagate Defender updates. The only allowed source for Defender updates is a shared folder (UNC path).
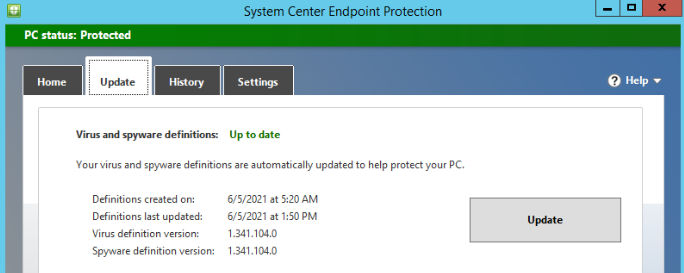
Opening System Center Endpoint Protection tool, you can see:

If you force system to update, you can read error message:

Malware definitions can be updated after additional configuration using registry:

Now, definition update process ends successfully:
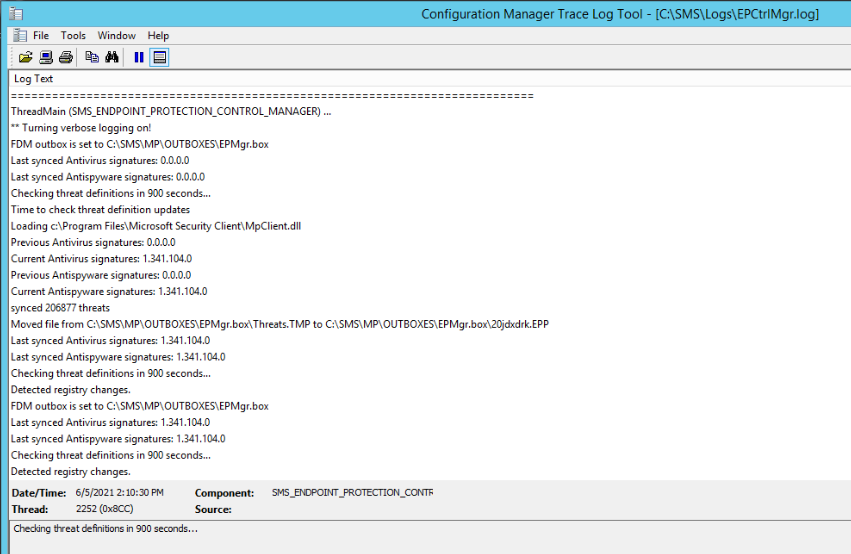
If you check EPCntrl.log entries, you can see updates are downloaded and passed to CM Site Server using standard communication via outbox:
SQL table is no more empty, simple query reveals records:

It should be noted, isolated Endpoint Protection Point must be configured with alternate (without using Internet connection) Defender updates source like UNC path. If Endpoint Protection Point can receive updates with existing Internet connection or using local WSUS, no additional configuration is needed.
 PL
PL